Man in the middle attack
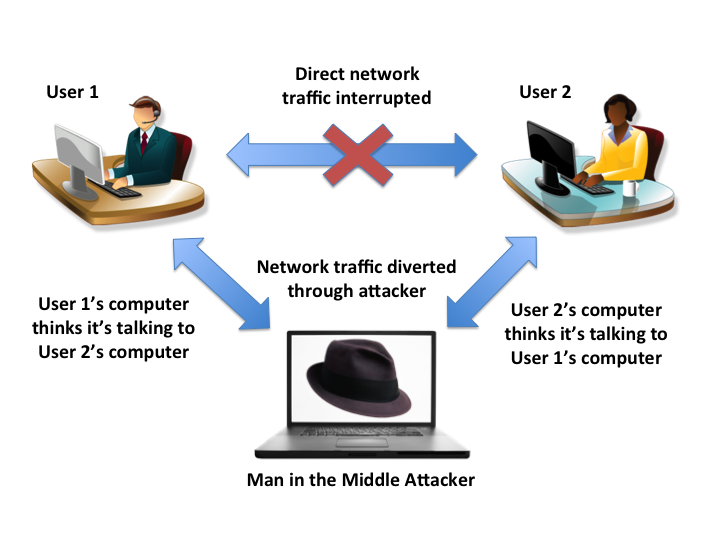
A man-in-the-middle (MITM) attack is an attack where the malicious actor attempts to intercept, read or alter information moving between two computers.
There are a variety of ways that attackers can insert themselves in the middle of your online communications.
- By distributing malware, a Trojan virus or a malicious script
- By exploiting the design vulnerabilities in the Wi-Fi networks
- By exploiting inherent and un-fixed vulnerabilities of an unpatched desktop browser,
- By exploiting vulnerabilities which are introduced due to a mis-configuration or non-hardening of the operating system
MITM attacks allows the attacker to :-
- Receive and request personal information posing as a trusted party (such as a website that you regularly use).
- Hijack a browser session and steal credit card number,personal detail etc.
- Deep dive insight into applications of a computer, and gain the usage pattern and other personal details of a person .
- Record an entire authentication session, decipher the userid and password information from it, which he can use to impersonate the victim and create damage to a greater extent
Having a correctly defined security perimeter defense design, server and network component’s hardening, implementing robust patch management system and following best security practices can help fix MITM attacks.
