Posts
How to create csr certificate and finally install digital certificate on tomcat server.
To generate a CSR and Private Key for Tomcat, perform the following steps:
Using the Java JDK Tool (Recommended JDK 1.4 or higher) , Keytool: Go into the JDK/bin/ directory (/j2sdk1.4.0/bin/)
STEP 1:
Using the java keytool command line utility, the first thing you need to do is create a keystore and generate the key pair. Do this with the following command:
keytool -genkey -keysize 2048 -keyalg RSA -alias [Alias name] -keystore [Keystore Name]
Enter keystore password: Choose a password and enter it when prompted to do so.
What is your first and last name?
[Unknown]: www.mydomain.com (example)
What is the name of your organizational unit?
[Unknown]: Thawte testing (example)
What is the name of your organization?
[Unknown]: Thawte Testing (example)
What is the name of your City or Locality?
[Unknown]: Cape Town (example)
What is the name of your State or Province?
[Unknown]: Western Province (example)
What is the two-letter country code for this unit?
[Unknown]: ZA (example)
Is CN=www.mydomain.com, OU=Thawte testing, O=Thawte Testing, L=Cape Town, ST=Western Province, C=ZA correct?
[no]: yes
Enter key password for <tomcat>
(RETURN if same as keystore password)
NOTE: Please specify the same password for the keystore and the keyentry or else you will receive the following error message when you restart the jakarta engine: “java.security.UnrecoverableKeyException: Cannot recover key”
Note, that a keystore was created.
Please run: keytool -list -keystore [keystorename] to make sure you can read the keystore file.
The keystore will be stored in your JDK/bin directory. Create a copy of the keystore file and store it on a removable disk for safe keeping in case of a server crash.
STEP 2:
Backup Keystore file: To backup the keystore file with the keyentry just created, please refer to the following solution: SO1870
STEP 3:
Generate a CSR off the newly create keystore and keyentry:
keytool -certreq -alias tomcat -keyalg RSA -file certreq.csr -keystore [keystorename]
Enter keystore password (from Step 1).
The CSR will be saved to your JDK/bin directory:
—–BEGIN NEW CERTIFICATE REQUEST—–
and
—–END NEW CERTIFICATE REQUEST—–
STEP 4:
Submit the CSR in online Certificate enrollment process and fax the necessary documentation to your certificate renewer.
Installation of certificate.
Problem:
Install certificate
Install certificate on Tomcat
Resolution:
Follow the instructions below to install the certificate on a Tomcat Server
Step 1: Download your Thawte certificate in PKCS#7 format
You will receive an email when your certificate is issued.
Retail Clients: Download your certificate in PKCS#7 format as per the instruction on the following solution:
To download your Thawte certificate, perform the following steps:
Access your Thawte account:
For Retail customers – Thawte Certificate Center (TCC):
https://ssl-certificate-center.thawte.com/process/retail/console_login?application_locale=THAWTE_US
For SPKI customers – Thawte Certificate Center Enterprise (TCCE): https://ssl-certificate-center-enterprise.thawte.com/vcce/enterprise/console_login?application_locale=THAWTE_US
For Reseller Partners – Thawte Partner Center: Please visit the following link: https://products.thawte.com/geocenter/reseller/logon.do
Enter your Username and Password.
Select the certificate from the list of available orders then click on Pick Up Certificate link.
Note: If you have a Code Signing certificate, skip steps 6 and 7. For steps to signing your code please view : AR1119
From the Format drop down box select the certificate format that is required. For help on which format to select, please refer to solution SO799
Click on the Copy button to highlight certificate then right click and select copy or keyboard shortcut (ctrl+c).
Paste the certificate into a text editor (ex. Notepad or Vi) and save it.
If you downloaded the PKCS#7 version, save the file with a .P7B extension.
If you downloaded the X.509 version, save the file with a .CER extension.
For the installation guide to the most common server types go to: SO1498
Note: If the server software is not listed proceed to follow the installation instructions outlined to you in your server software documentation.
Reseller Clients (bought certificate through a third party): Download your certificate in PKCS#7 format, refer to solution
Resolution
To download issued Thawte SSL certificate through User Portal, perform the following steps:
Access Thawte User Portal
Visit https://products.thawte.com/orders/orderinformation/authentication.do
Provide the common name, technical contact e-mail address associated with the SSL order, and the image number generated from the Thawte User Authentication page.
Select Request Access against the correct order ID.
An e-mail will be sent to the technical contact e-mail address specified above.
Click on the link listed in the e-mail to enter the User Portal.
Click View Certificate Information.
Copy and Paste your Thawte certificate to Notepad and save as a cert.p7b
Step 2: Install the SSL certificate
Import the certificate into the Java keystore using the following keytool command:
keytool -import -alias tomcat -trustcacerts -file cert.p7b -keystore [keystorename]
Alternate installation instructions if the X.509 certificate is downloaded instead.
Follow Step 1 by downloading an X.509 certificate file format.
Download both Primary and Secondary Intermediate certificate as separate files, refer to article.
Thawte Intermediate and Cross Certificate CAs
Description
Thawte uses Intermediate CAs to enhance the security of SSL and Code Signing certificates. Installing the correct Intermediate CAs or CA bundle for the certificate being used is absolutely essential to ensure that users don’t see certificate errors when visiting a website or running software secured with a Thawte certificate.
The following tables list Thawte products with links to the relevant Intermediate CA certificates and CA bundles. Please read the following notes to determine which you need:
Microsoft IIS : If you obtained your SSL certificate in the PKCS#7 format from your Thawte Certificate Center (TCC) account, downloading and manually installing CA certificates shouldn’t be required. If however you installed your SSL certiifcate from the approval email, please obtain the proper Intermediate CA below and see kb solution SO14996 for installation instructions
Tomcat : Customers that selected these server platforms when enrolling will have received a version of their certificate containing the SSL certificate and all required Intermediate CAs (as a PKCS#7 bundle). Downloading and manually installing CA certificates shouldn’t be required.
Apache and Apache derivatives
Apache HTTPD, other Apache derivatives and many webhosting providers are only able to specify a single CA certificate in the server or host configuration; these customers should download a CA bundle containing the relevant Intermediate and Cross Root CAs.
Other server platforms :
Please consult the server documentation or search our Knowledge Base to determine which format is required. In many cases, separate Intermediate and Cross Root CAs are needed.
Select the Intermediate CAs link based on your certificate product type. Once you have the SSL certificate, Primary and Secondary Intermediate CA certificate files, begin the import process.
Note: It is imperative the installation of Primary Intermediate CA, Secondary Intermediate CA and SSL certificate on the keystore is followed below.
Import the Primary Intermediate certificate (e.g., use alias: primary)
keytool -import -alias primary -trustcacerts -file primary_intermediate_file_name -keystore [keystorename]
Import the Secondary Intermediate certificate (e.g., use alias: secondary)
keytool -import -alias secondary -trustcacerts -file secondary_intermediate_file_name -keystore [keystorename]
Import the SSL certificate (Use the same alias name based on the created keystore and submitted CSR from Thawte)
keytool -import -alias [your_alias_name] -trustcacerts -file X.509_file_name -keystore [keystorename]
Note: Tomcat keeps its configuration information in the server.xml file. Configure Tomcat to reference the correct keystore and keystore password as shown in the following solution:
Enable SSL in Tomcat with server.xml
Problem
Enable SSL in Tomcat with server.xml
Configuring the SSL Connector in server.xml
Resolution
To configure the SSL in Tomcat with server.xml follow the instructions below:
1. Shutdown Tomcat, if it is running. Changes to the file <JWSDP_HOME>/conf/server.xml are read by Tomcat when it is started.
2. Open the file <JWSDP_HOME>/conf/server.xml in a text editor.
3. Find the following section of code in the file (try searching for SSL Connector). Remove comment tags around the Connector entry. The comment tags that are to be removed are shown in blue below.
<!– SSL Connector on Port 8443 –>
<!–
<Connector
className=”org.apache.coyote.tomcat4.CoyoteConnector”
port=”8443″ minProcessors=”5″
maxProcessors=”75″
enableLookups=”false”
acceptCount=”10″
connectionTimeout=”60000″ debug=”0″
scheme=”https” secure=”true”>
<Factory
className=”org.apache.coyote.tomcat4.CoyoteServerSocketFactory”
clientAuth=”false” protocol=”TLS”
keystoreFile=/”insert path to the keystore here”>
keystorePass=”insert keystore password here”/>
</Connector>
–>
4. Save and close the file.
5. Start Tomcat.
For tomcat 6 please view: http://tomcat.apache.org/tomcat-6.0-doc/ssl-howto.html
Tomcat runs SSL over port 8443. Make sure that this port is enabled on the Tomcat server and any firewalls/proxies this server may lie behind.
For additional trouble shooting steps regarding “keytool error: java.lang.Exception: Input not an X.509 certificate” refer to solution
Troubleshooting Error: “keytool error: java.lang.Exception: Input not an X.509 certificate”
Problem
Error occurs when importing Sun Java™ certificate into the Key store:
keytool error: java.lang.Exception: Input not an X.509 certificate
Cause
There are a few causes for this error:
1. The incorrect alias was specified while trying to import the Certificate.
2. The Certificate being imported is improperly formatted.
3. The Certificate is imported into the incorrect keystore.
Resolution
Please review each of the ‘possible’ causes below and their fixes to troubleshoot this error:
1. The incorrect alias was specified while trying to import the Certificate.
2. The Certificate being imported is improperly formatted.
NOTE: Try add 2 carriage returns at the end of the downloaded certificate file.
3. The Certificate is imported into the incorrect keystore.
If the keystore is lost a new keystore will need to be generated, and the certificate reissued
Courtesy : Thawte
Install Self Signed Exchange 2010 SSL certificate
For my example, my domains are…
Local domain: vcp.local
Outside domain: vcpdomain.com.au
#NETBIOS name of Client Access exchange server: vcpsydex01
#Internal FQDN (AD name): vcpsydex01.vcp.local
#External FQDN (Public name): smtp.vcdomain.com.au
#Autodiscover name: autodiscover.vcdomain.com.au
#SubjectName: cn=smtp.vcdomain.com.au
Run the following command on the Client Access Server for generating the new Self-Signed SSL cert using the names listed above:
New-ExchangeCertificate -FriendlyName “SelfSigned Cert” -SubjectName “cn=smtp.vcdomain.com.au” -DomainName vcpsydex01,vcpsydex01.vcp.local,smtp.vcdomain.com.au, autodiscover.vcdomain.com.au -PrivateKeyExportable $True
Prior to Windows Vista SP1, the Windows RPC/HTTP client-side component required that the Subject Name (aka Common Name) on the certificate match the “Certificate Principal Name” configured for the Outlook Anywhere connection in the Outlook profile. Therefore, as a best practice, you should ensure that smtp.vcdomain.com.au is listed as the Subject Name in your certificate unless you plan on changing the configuration which can be achieved by using the Set-OutlookProvider cmdlet with the -EXPR parameter as described in http://msexchangeteam.com/archive/2008/09/29/449921.aspx.
Open IIS on the Exchange Server and tell it to use this certificate.
- Click on the Default Web Site
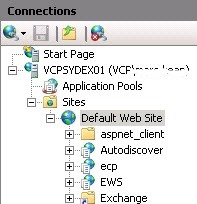
- Click Bindings on the right
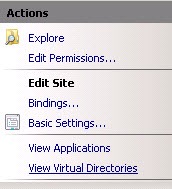
- Select HTTPS, and choose edit
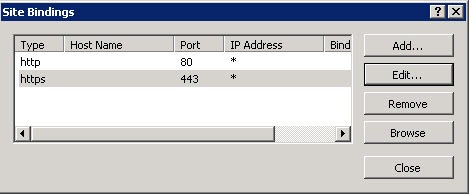
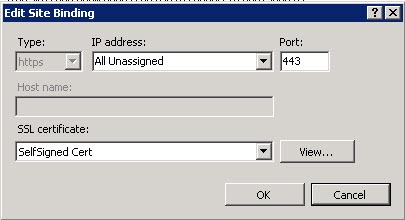
- Under SSL certificate, click the drop down list and choose your certificate that you created earlier.
- You need to setup the following external DNS entries 1. smtp.vcdomain.com.au 2. autodiscover.vcdomain.com.au, these need to point to the external IP address of your Exchange CAS server.
The next few steps are to install the certificate to the Clients. - From Internet Explorer, navigate to the website of your OWA, https://mail.vcdomain.com/owa Click on Certificate Error, then click View certificates.
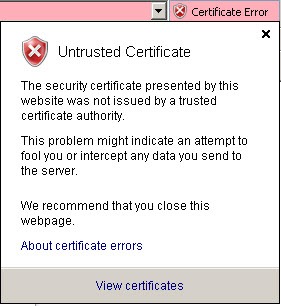
- Click Install Certificate

- Click Next
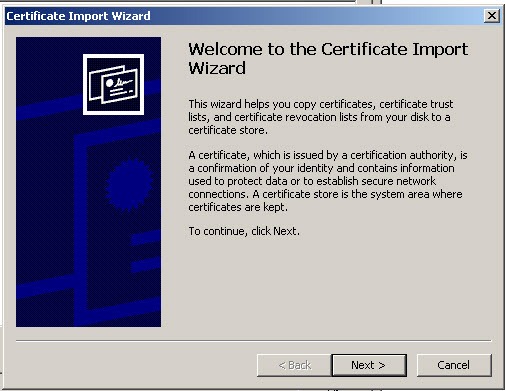
- Select the second option
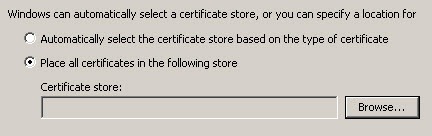
- Select the box Show Physical Stores, Under Trusted Root Certification Authorities, select Registry and click OK
Please note, you will need to repeat this step again and choose Local Computer.
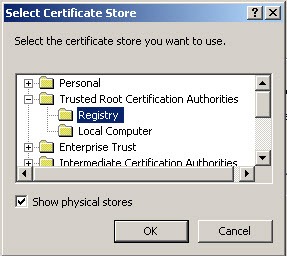
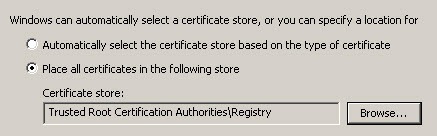
- Click Finish
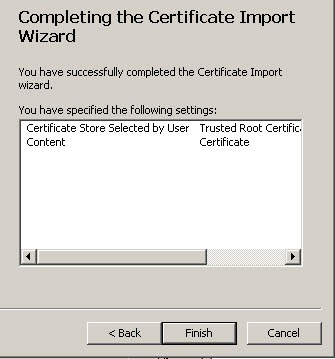
- Select Yes. Close and re-open Internet Explorer.
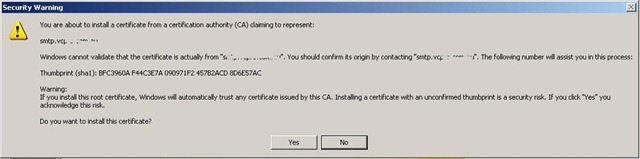
- Close and restart Internet Explorer.
For more information, please refer to http://msexchangeteam.com/archive/2007/07/02/445698.aspx





