The Complete Guide to Email Authentication

Introduction
The objective of this paper is to provide a brief overview and description of the most commonly used email authentication practices and methodologies. It is not exhaustive in nature, and does not cover every aspect of every technology in use today. It does, however, cover the main topics and points of discussion with regard to the mainstream standards used today for authenticating email.
Spam and Other Online Threats
In a recent report released by Cisco Systems, it was revealed that nearly 200 billion spam email messages are sent each day – approximately 90% of worldwide email. Other online threats that were cited include phishing, botnets, social engineering, and reputation hijacking – all used in collaboration with spamming. Because spam and other cyber security issues continue to increase year after year, technology integrators have turned to alternative methods to secure their communications. Email authentication is one such method, along with a wide set of other tools used by email senders and receivers to establish sender reputation.
Email Authentication
Generally defined, email authentication is a multi-method approach to securing email communications using either IP based and/or cryptographic standards. Email senders create a public record that verifies that their sending domain is authorized to send email from a particular IP address or mail server. Receiving ISPs can then use this record to validate the legitimacy of the sender and the messages they are sending. Additionally, ISPs commonly use this validation along with other metrics to determine the reputation of a sender, and ultimately if they will deliver the sender’s messages.
There are currently four different methods or standards that are typically used to authenticate email today: Sender Policy Framework (SPF), Sender ID, DomainKeys, and DomainKeys Identified Mail (DKIM). Each standard authenticates using a different methodology. While a sender can authenticate using all of the standards, an ISP may choose to only verify one or more of them.
Email Spoofing
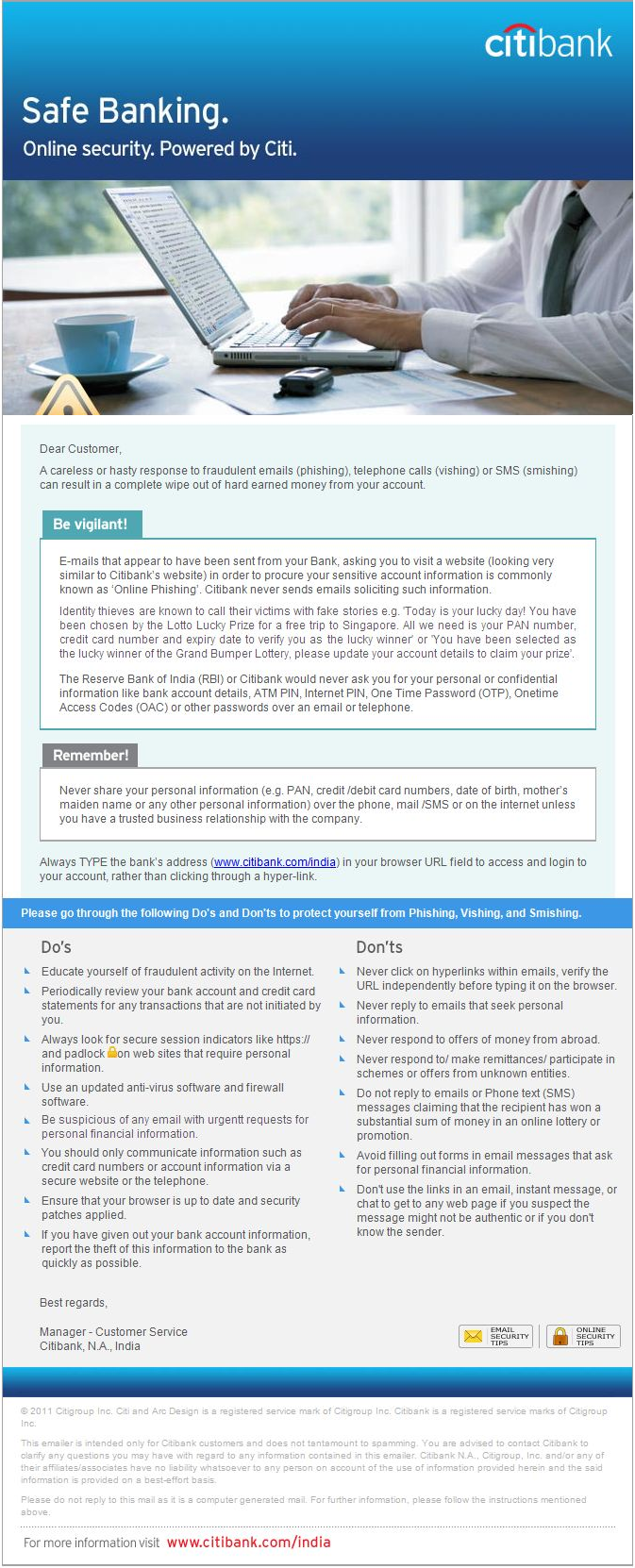
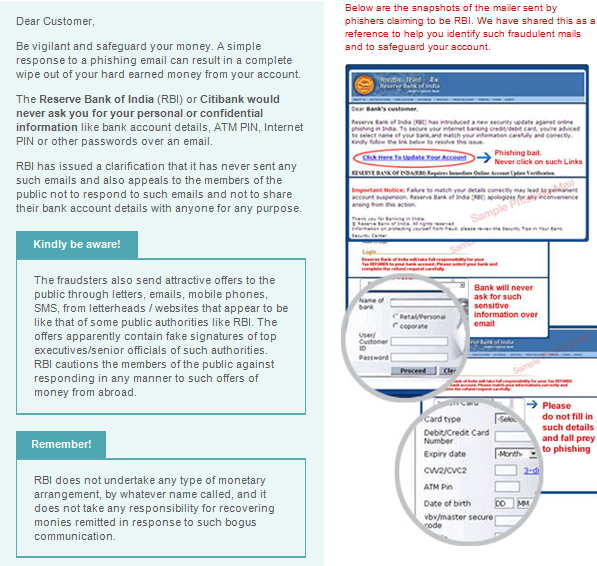
One of the main benefits to using email authentication is that it dramatically reduces the problem of email forging or spoofing (also known as phishing) – where a user will receive an email that appears to originate from one source, when in reality it was sent from another source. Email spoofing is a classic spammer tactic used to coerce unsuspecting users into disclosing secure or confidential information without their knowledge or authorization.
A classic example of email spoofing that still occurs today are emails purportedly from a bank or financial institution, alerting the user that their account has been compromised and, in order to resolve the situation, they must click the link in the email to log into their account. Both the link, as well as the sender information have been spoofed or forged to look as if the message came from the purported bank.
Courtesy – http://www.socketlabs.com/blog/the-complete-guide-to-email-authentication-part-1/