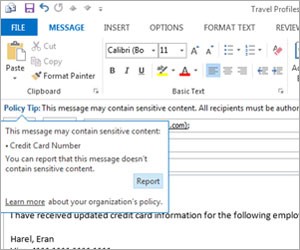
The Risk of Running Windows XP After Support Ends April 2014
Back in April I published a post about the end of support for Windows XP called The Countdown Begins: Support for Windows XP Ends on April 8, 2014. Since then, many of the customers I have talked to have moved, or are in the process of moving, their organizations from Windows XP to modern operating systems like Windows 7 or Windows 8.
There is a sense of urgency because after April 8, Windows XP Service Pack 3 (SP3) customers will no longer receive new security updates, non-security hotfixes, free or paid assisted support options or online technical content updates. This means that any new vulnerabilities discovered in Windows XP after its “end of life” will not be addressed by new security updates from Microsoft. Still, I have talked to some customers who, for one reason or another, will not have completely migrated from Windows XP before April 8. I have even talked to some customers that say they won’t migrate from Windows XP until the hardware it’s running on fails.
What is the risk of continuing to run Windows XP after its end of support date? One risk is that attackers will have the advantage over defenders who choose to run Windows XP because attackers will likely have more information about vulnerabilities in Windows XP than defenders. Let me explain why this will be the case.
When Microsoft releases a security update, security researchers and criminals will often times reverse engineer the security update in short order in an effort to identify the specific section of code that contains the vulnerability addressed by the update. Once they identify this vulnerability, they attempt to develop code that will allow them to exploit it on systems that do not have the security update installed on them. They also try to identify whether the vulnerability exists in other products with the same or similar functionality. For example, if a vulnerability is addressed in one version of Windows, researchers investigate whether other versions of Windows have the same vulnerability. To ensure that our customers are not at a disadvantage to attackers who employ such practices, one long standing principle that the Microsoft Security Response Center (MSRC) uses when managing security update releases is to release security updates for all affected products simultaneously. This practice ensures customers have the advantage over such attackers, as they get security updates for all affected products before attackers have a chance to reverse engineer them.
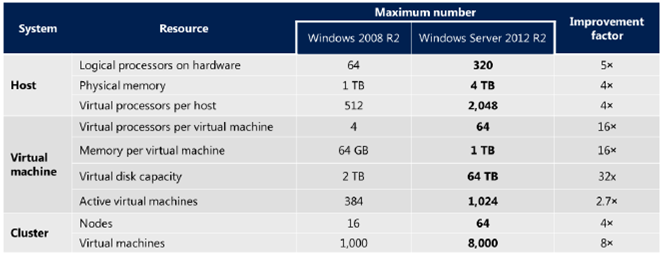
But after April 8, 2014, organizations that continue to run Windows XP won’t have this advantage over attackers any longer. The very first month that Microsoft releases security updates for supported versions of Windows, attackers will reverse engineer those updates, find the vulnerabilities and test Windows XP to see if it shares those vulnerabilities. If it does, attackers will attempt to develop exploit code that can take advantage of those vulnerabilities on Windows XP. Since a security update will never become available for Windows XP to address these vulnerabilities, Windows XP will essentially have a “zero day” vulnerability forever. How often could this scenario occur? Between July 2012 and July 2013 Windows XP was an affected product in 45 Microsoft security bulletins, of which 30 also affected Windows 7 and Windows 8.
Some of the people I have discussed this scenario with are quick to point out that there are security mitigations built into Windows XP that can make it harder for such exploits to be successful. There is also anti-virus software that can help block attacks and clean up infections if they occur. The challenge here is that you’ll never know, with any confidence, if the trusted computing base of the system can actually be trusted because attackers will be armed with public knowledge of zero day exploits in Windows XP that could enable them to compromise the system and possibly run the code of their choice. Furthermore, can the system’s APIs that anti-virus software uses be trusted under these circumstances? For some customers, this level of confidence in the integrity of their systems might be okay, but for most it won’t be acceptable.
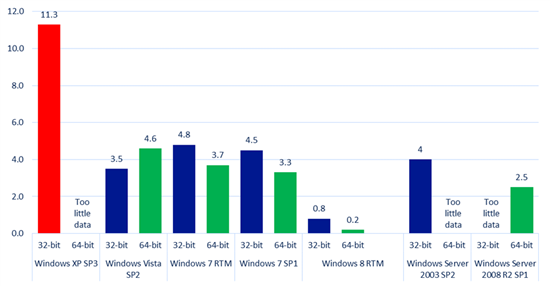
As for the security mitigations that Windows XP Service Pack 3 has, they were state of the art when they were developed many years ago. But we can see from data published in the Microsoft Security Intelligence Report that the security mitigations built into Windows XP are no longer sufficient to blunt many of the modern day attacks we currently see. The data we have on malware infection rates for Windows operating systems indicates that the infection rate for Windows XP is significantly higher than those for modern day operating systems like Windows 7 and Windows 8.
Figure 1: Infection rate (CCM) by operating system and service pack in the fourth quarter of 2012 as reported in the Microsoft Security Intelligence
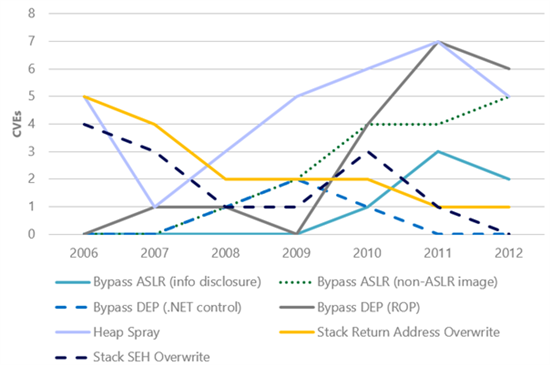
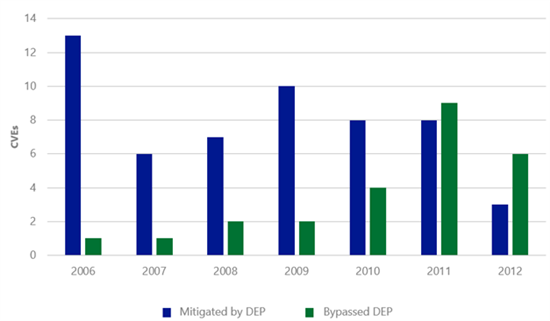
I recently wrote about the findings of a new study on exploit activity that we just published: Software Vulnerability Exploitation Trends – Exploring the impact of software mitigations on patterns of vulnerability exploitation. This seven-year study indicates that attackers have evolved their attacks to overcome one of the key security mitigations that Windows XP has: Data Execution Prevention (DEP). Figure 3 shows the number of common vulnerabilities and exposures (CVEs) that had exploits that would have been mitigated if DEP were enabled compared to the number of CVEs that had exploits that bypassed DEP. With the exception of 2007 and 2008, there appears to be a clear downward trend in DEP’s ability to retroactively break exploits. This trend is not because DEP is no longer effective; rather, it is an indication that attackers have been forced to adapt to environments in which DEP is already enabled—at increased cost and complexity. The evidence is the increasing number of CVEs that had exploits that bypassed DEP.
Figure 2 (left): The number of CVEs that were exploited using specific exploitation techniques; Figure 3 (right): The number of CVEs for which exploits were written that could have been mitigated by enabling DEP as compared to the number of CVEs that had exploits that bypassed DEP
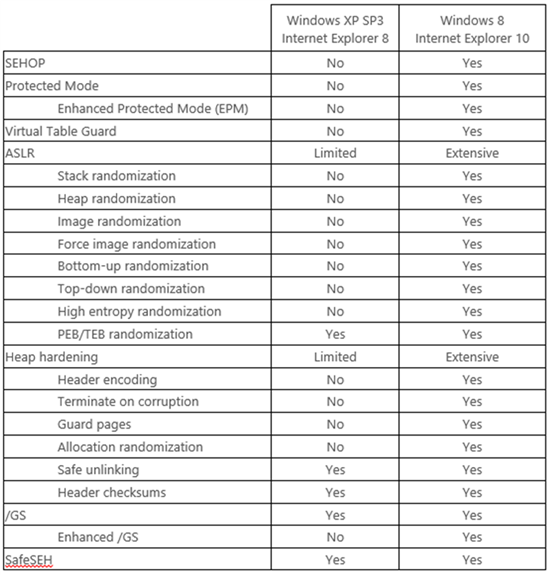
This new data shows us that the predominate threats that individuals and organizations face are now much different than they were when Windows XP Service Pack 3 was released. Turning on the Windows Firewall in Windows XP Service Pack 2 and later operating systems forced attackers to evolve their attacks. Rather than actively targeting remote services, attackers now primarily focus on exploiting vulnerabilities in client applications such as web browsers and document readers. In addition, attackers have refined their tools and techniques over the past decade to make them more effective at exploiting vulnerabilities. As a result, the security features that are built into Windows XP are no longer sufficient to defend against modern threats. Windows 8 has significantly superior security mitigations compared to Windows XP as Figure 4 illustrates. Detailed information on the new security mitigations built into Windows 8 is available in the aforementioned research paper.
Figure 4: The table below compares the mitigation features supported by Internet Explorer 8 on Windows XP Service Pack 3 with the features supported by Internet Explorer 10 on Windows 8. As this table shows, Internet Explorer 10 on Windows 8 benefits from an extensive number of platform security improvements that simply are not available to Internet Explorer 8 on Windows XP.
Organizations need a level of certainty about the integrity of their systems. Minimizing the number of systems running unsupported operating systems is helpful in achieving that. End of support for Windows XP is April 8, 2014.
Reference by http://www.microsoft.com