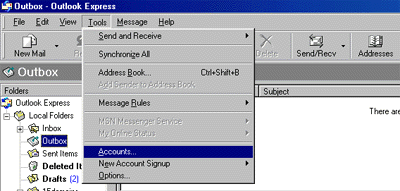
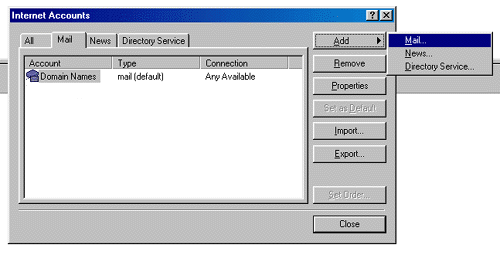
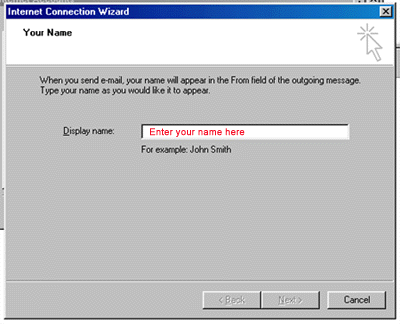
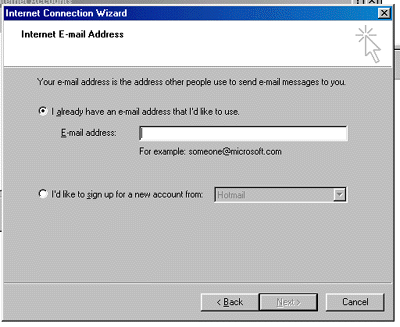
Recognized annually on January 28th, Data Privacy Day is defined as a centered approach towards respecting privacy, safeguarding data, and enabling trust. It is a global effort to raise and promote awareness around protecting one’s data and privacy. With this thought in mind, we have put together these 10 security tips on Data Privacy Day.
10 Security Tips on Data Privacy Day
1. Change the passwords of your online accounts. Here are some tips to build strong and unique ones:
- Use a mix of uppercase and lower letters
- Use special characters
- Use numbers
- Use at least 8 characters
Also, here’s a fun way to create a password that is strong and can be easily remembered. First, think of a phrase or the title of your favorite book or movie; say, “The Girl With The Dragon Tatoo”. Now, take the first letter of every word in the title – this will give you tgwtdt. Capitalize a letter, add some numbers, and special characters – and you will have the ultimate password Tgwtdt#$8945B. We tested the strength of this password, and it seems that a hacker will take about 273 years to crack it. Find it out yourself – https://www-ssl.intel.com/content/www/us/en/forms/passwordwin.html
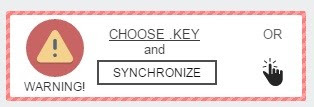
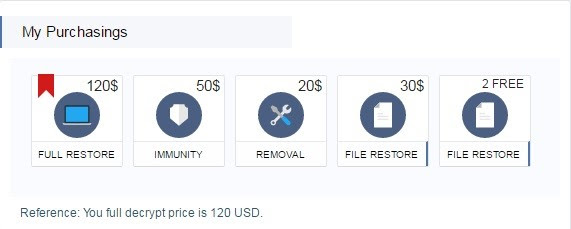
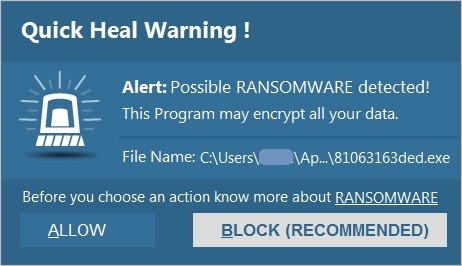
2. Take a back up of all your important data stored on your computer and mobile device. You can either take the backup over Cloud or an external hard drive. Taking regular data backups can save you from the aftermath of a virus attack or system crash – especially a ransomware infection. Ransomware is a malware that hijacks your data and demands money (ransom) to release it.
3. Data Privacy Day is not only about storing or saving data. It also advocates the importance of disposing of your information securely. Data that you delete from your computer or mobile device does not really get deleted permanently. It can still be recovered with advanced data recovery tools. So, while removing sensitive information, ensure it is gone forever. Know how to delete your data securely.
4. It is unsafe to store login ID and passwords, banking details, social security number, and other such sensitive information on your mobile device or computer. But, if you can’t help it, ensure that the data is encrypted. When you encrypt an information, it gets converted into an unreadable form, and can only be read by you. So, even if a situation arises wherein your data falls into the wrong hands, you can rest assured that it won’t get misused.
5. Just like you won’t hand over your wallet, ID card, or house key to a stranger, avoid sharing your personal information on the Internet; these could be unfamiliar websites, survey forms, online friends, unsolicited emails, and anything/anybody that asks for your information. When it comes to Data Privacy, it’s wise to be a miser in sharing your data.
6. Banking or shopping online using unsecured Wi-Fi networks can let attackers steal your personal and financial information. While using any such network, ensure it is accessible only with a login ID and password.
7. Before installing any mobile app, review its permissions carefully. Many a time, you may come across an app that asks for permissions that are not actually required for it to function on your device. For instance, if a simple Flash Light app is asking your permission to access your device’s Internet, contact details, photos, etc., then chances are it is a malicious or a potentially dangerous app. So, stay cautious against such threats.
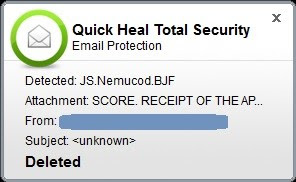
8. One of the greatest threats to your data and privacy is phishing. Phishing is defined as an attempt to trick you into providing your personal or financial details so that the attacker can commit illegal acts using your name. Any unknown or unexpected communication (email, call, SMS, etc.) that carries a sense of urgency and requires you to provide your personal information should be treated as a phishing attack. Always ignore such communications and report them to the right authority.
9. With mobile devices becoming an integral part of our everyday lives, they store massive amounts of data about us, our friends and family members. More importantly, being smaller and compact, they are more vulnerable to theft. So, it is only logical to protect these devices with a PIN, fingerprint or a password. We do not recommend the Pattern Lock because they are easily noticeable and less secure. Also, it is wise to keep the Automatic Lock feature ON at all times.
10. While you follow all the steps mentioned above, also consider getting a trusted antivirus solution. The software that you choose must offer multiple layers of security that can block ransomware, fake, infected and phishing websites, emails designed for phishing attacks, malicious downloads, and unauthorized data storage devices.
Reference by Quick Heal