How to enable legacy for sata hard drive in HP?
To Enter the BIOS setup
Try any one of the following key’s on HP Server
Esc; DEL; F1; F2; F10; Ctrl +S
Go to Advance
Select on Harddisk Configuration
Click on Sata Mode Selection
Select AHCI
To Enter the BIOS setup
Try any one of the following key’s on HP Server
Esc; DEL; F1; F2; F10; Ctrl +S
Go to Advance
Select on Harddisk Configuration
Click on Sata Mode Selection
Select AHCI
An email is enough to rob you of your hard-earned money !
Phishing email alert : Stay away from phishing emails claiming to be from Reserve Bank of India.
we thought to update you about the ongoing dangers lurking over your bank account. Reproduced here is a fake email supposedly sent by Reserve Bank of India (RBI), that is being circulated on the internet.


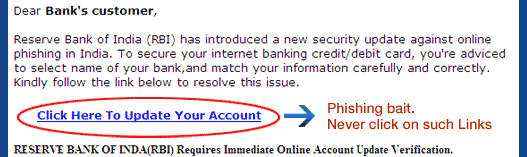
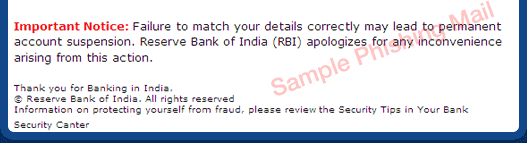


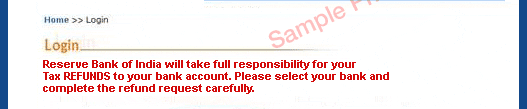

Such mails are fradulent. Request you not to respond to such emails. Be aware and be alert. In case you have clicked on any links within such an email and /or shared any sensitive data, please contact your nearest Bank Bank branch or write to you bank support email id or call your bank customer care and inform them and take a next guidelines.
Courtesy : got email from HDFC Bank Ltd.
How to check date?
Type date command
#date
Thu May 12 15:43:04 IST 2011 (Shown on today date)
How to set date and time?
For example, set new data to 2 Oct 2006 18:00:00, type the following command as root user:
# date -s "2 OCT 2006 18:00:00"
OR
# date --set="2 OCT 2006 18:00:00"
You can also simplify format using following syntax:
# date +%Y%m%d -s "20081128"
To set time use the following syntax:
# date +%T -s "10:13:13"
Where,
Use %p locale’s equivalent of either AM or PM, enter:
# date +%T%p -s "6:10:30AM"
# date +%T%p -s “12:10:30PM”
Courtesy :-http://www.cyberciti.biz/
A firewall is a part of a computer system or network that is designed to block unauthorized access while permitting authorized communications.
It is a device or set of devices that is configured to permit or deny network transmissions based upon a set of rules and other criteria.
Firewalls are thus a specialized type of router focusing on specific types of network security functions.
Firewalls can be implemented in either hardware or software, or a combination of both.
Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets.
All messages entering or leaving the intranet pass through the firewall, which inspects each message and blocks those that do not meet the specified security criteria.
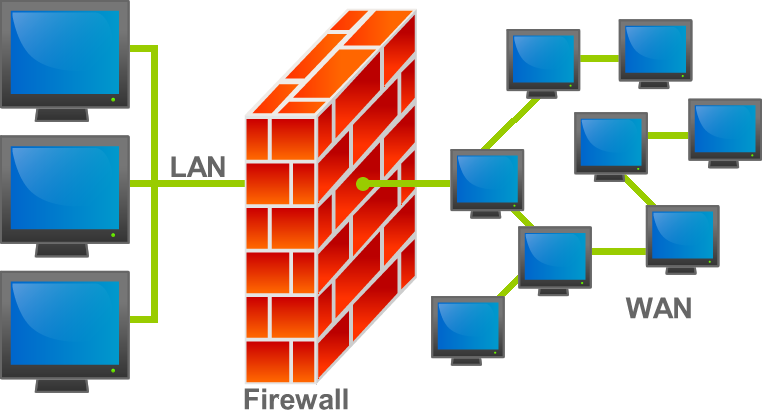
Courtesy :- http://en.wikipedia.org/wiki/Firewall_(computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system
Trojan horses may allow a hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system, a hacker may have access to the computer remotely and perform various operations, limited by user privileges on the target computer system and the design of the Trojan horse.
Courtesy :- http://en.wikipedia.org/wiki/Trojan_horse_(computing)
Phishing is an Internet scam where the user is convinced to give valuable information. Phishing will redirect the user to a different website through emails,instant messages, spywares etc.Phishers offer illegitimate website to user to fill personal information.The main purpose of phishing is to get access to the customer’s bank accounts,passwords and other security information. Phishing attacks can target the audience through mass-mailing millions of emai address aroung the world.
Phishers can fool user by convincing them to get into a fake website with the domain name slightly different from the orignal website which is difficult to notice.
They use the images of the legitimate hyperlink,which itself helps as a hyperlink to an unathorized website. Phishers track the users by using the images in the content of a web page that looks like a browser window. Keeping an unathorized browser window on top of, or next to a legitimate window having same looks,
will make the user believe that they are from the same source. Setting the tone of the languages same as the original website.
Courtesy :- http://www.eccouncil.org/
Courtesy :- Microsoft Corporation
http://www.microsoft.com/security/spyware/indicators.aspx
Spyware is software that aims to gather information about a person or organization without their knowledge and
that may send such information to another entity without the consumer’s consent, or that asserts control over a computer without the consumer’s knowledge.
“Spyware” is mostly classified into four types: system monitors, trojans, adware, and tracking cookies.
Spyware is mostly used for the purposes of tracking and storing Internet users’ movements on the Web and serving up pop-up ads to Internet users.
Whenever spyware is used for malicious purposes, its presence is typically hidden from the user and can be difficult to detect.
Some spyware, such as keyloggers, may be installed by the owner of a shared, corporate, or public computer intentionally in order to monitor users.
While the term spyware suggests software that monitors a user’s computing, the functions of spyware can extend beyond simple monitoring.
Spyware can collect almost any type of data, including personal information like internet surfing habits, user logins, and bank or credit account information.
Spyware can also interfere with user control of a computer by installing additional software or redirecting web browsers.
Some spyware can change computer settings, which can result in slow Internet connection speeds, un-authorized changes in browser settings, or changes to software settings.
Sometimes, spyware is included along with genuine software, and may come from a malicious website.
In response to the emergence of spyware, a small industry has sprung up dealing in anti-spyware software.
Running anti-spyware software has become a widely recognized element of computer security practices, especially for computers running Microsoft Windows.
A number of jurisdictions have passed anti-spyware laws, which usually target any software that is surreptitiously installed to control a user’s computer.

Routes of infection:-
Spyware does not necessarily spread in the same way as a virus or worm because infected systems generally do not attempt to transmit or copy the software to other computers.
Instead, spyware installs itself on a system by deceiving the user or by exploiting software vulnerabilities.
Most spyware is installed without users’ knowledge, or by using deceptive tactics.
Spyware may try to deceive users by bundling itself with desirable software. Other common tactics are using a Trojan horse.
Some spyware authors infect a system through security holes in the Web browser or in other software.
When the user navigates to a Web page controlled by the spyware author, the page contains code which attacks the browser and forces the download and installation of spyware.
The installation of spyware frequently involves Internet Explorer. Its popularity and history of security issues have made it a frequent target.
Its deep integration with the Windows environment make it susceptible to attack into the Windows operating system.
Internet Explorer also serves as a point of attachment for spyware in the form of Browser Helper Objects, which modify the browser’s behavior to add toolbars or to redirect traffic
Effects and behaviors
A spyware program is rarely alone on a computer: an affected machine usually has multiple infections. Users frequently notice unwanted behavior and degradation of system performance.
A spyware infestation can create significant unwanted CPU activity, disk usage, and network traffic. Stability issues, such as applications freezing, failure to boot, and system-wide crashes are also common.
Spyware, which interferes with networking software, commonly causes difficulty connecting to the Internet.
In some infections, the spyware is not even evident. Users assume in those situations that the performance issues relate to faulty hardware, Windows installation problems, or another infection.
Some owners of badly infected systems resort to contacting technical support experts, or even buying a new computer because the existing system “has become too slow”.
Badly infected systems may require a clean reinstallation of all their software in order to return to full functionality.
Moreover, some types of spyware disable software firewalls and anti-virus software, and/or reduce browser security settings, which further open the system to further opportunistic infections.
Some spyware disables or even removes competing spyware programs, on the grounds that more spyware-related annoyances make it even more likely that users will take action to remove the programs.
Keyloggers are sometimes part of malware packages downloaded onto computers without the owners’ knowledge.
Some keyloggers software is freely available on the internet while others are commercial or private applications.
Most keyloggers allow not only keyboard keystrokes to be captured but also are often capable of collecting screen captures from the computer.
A typical Windows user has administrative privileges, mostly for convenience. Because of this, any program the user runs has unrestricted access to the system.
As with other operating systems, Windows users are able to follow the principle of least privilege and use non-administrator accounts.
Alternatively, they can also reduce the privileges of specific vulnerable Internet-facing processes such as Internet Explorer.
Courtesy :- wikipedia.org
A computer worm is a software program that is designed to copy itself from one computer to another, without human interaction. Unlike a computer virus, a worm can copy itself automatically.
Worms can replicate in great volume. For example, a worm can send out copies of itself to every contact in your e-mail address book, and then it can send itself to all of the contacts your contact’s e-mail address books.
Some worms spread very quickly. They clog networks and can cause long waits for you (and everyone else) to view Web pages on the Internet.
Courtesy :- Microsoft Corporation
http://www.microsoft.com/security/worms/whatis.aspx