It is important to figure out why your email bounces. If you receive an email bounce, you can look in the bounce message to find the proper error code that will give you the reason for the bounce. Below is a list of the Standard SMTP error codes and the Extended SMTP (ESMTP) error codes.
SMTP Error Codes
This list of codes is the standard SMTP error codes you will find in most email bounces.
Specific Explanation of the 400 Error Codes occurring on our servers:
450 4.1.8 : Sender address rejected: Domain not found
Our inbound servers require that the hostname for the sender server should have valid MX or A records in order to accept emails from it. You need to contact the sending server’s email admin to add valid DNS records for his server.
450 4.7.1 Client host rejected: cannot find your reverse hostname
Our inbound servers require reverse hostname for sender server IP to be present in order to accept the email. Please ensure that the valid PTR records are added for all outbound server IP’s. Post adding the required rDNS records our inbound servers will accept mails from the remote mail hosting server.
450 4.7.1 : Recipient address rejected: Policy Rejection- Quota Exceeded
This error comes from our incoming mail server if user is receiving excessive amounts of mails.
450 4.7.1 Recipient address rejected: Access denied.
This occurs when the recipient address is invalid. i.e., not in form of user@domainname OR if the Recipient address is blocked on server.
451 4.3.5 Server configuration problem – try again later;
451 4.7.1 Service unavailable – try again later;
This error most likely occurs if there is a configuration error with our servers. If you encounter any of the above messages, please contact our support helpdesk with the details.
452 4.5.3 Error: too many recipients
The error message is encountered when the user is exceeding the limit of more than 50 recipients in an email. The list of recipients is inclusive of To, Cc, and Bcc. If you encounter the above error, reduce the number of recipients in the email and try again.
Specific Explanation of the 500 Error Codes occurring on our servers:
522 5.7.1 : Recipient address rejected: Requested mail action aborted: exceeded storage allocation
This error comes if the user is overquota.
530 5.7.0 Recipient address rejected: Authentication Required.
This error comes when your sending mails to remote domain without using SMTP authentication.
550 5.1.1 Recipient address rejected: User unknown in virtual alias table;
This is the bounce back message that is received by the sender from our server if the destination email address does not exist.
The same error message is received if the recipient has a mail loop. That is, if the recipient has set a forward to another email address and that email address is forwarded back to the original one. In this case, you need to remove the loop in order to receive the emails.
If there is a forward set for an account, and an email is sent to that account, if for some reason the forwarded email is not sent, the original sender may get the above error.
For example, [email protected] if forwarded to [email protected], if a third user [email protected] emails to [email protected], he may get the above error if the forwarded email is bounced.
550 5.1.1 Protocol error
This error code ideally suggests that the sender has used SMTP protocol instead of ESMTP, thus the outbound mail of the sender was rejected. In short, the sending client doesn’t properly communicate and makes errors in the SMTP protocol.
550 5.3.2 Service currently unavailable
The error code 5.3.2 usually means that the system is not accepting network messages. We would thus need to look outside Exchange for a connectivity problem.
The error code ideally occurs ideally for two reasons which are listed below:
1). The sending IP is blacklisted at an RBL or blacklist monitoring site. (You may verify the same by inputting the IP via this link: http://mxtoolbox.com/blacklists.aspx )
2). There is a temporary block on the IP on our Inbound server due to multiple mails from this IP. Feel free to contact our support desk for more information and regarding de-listing the same.
3). If sending IP does not have a reverse PTR record configured. Reference URL: http://mxtoolbox.com/NetworkTools.aspx
550 5.4.5 Recipient address rejected: Hourly domain sending quota exceeded
This is the error message that you get if your domain name exceeds the hourly quota set for the domain name. Here, the term ‘hour’ refers to the last 60 minutes.
550 5.4.6 Recipient address rejected: Hourly sending quota exceeded
This is the error message that you get if the user (that particular email address) exceeds the hourly quota set. Here, the term ‘hour’ refers to the last 60 minutes.
550 5.7.1: Helo command rejected: You aren’t localhost.
550 5.7.1: Helo command rejected: You aren’t localhost.localdomain.
550 5.7.1: Helo command rejected: You are not me
Our servers do not accept SMTP HELO command as HELO localhost or HELO localhost.localdomain or HELO . We accept HELO from a valid Domain Name or your computer name which is other than your domain name. Please check with your ISP or Mail administrator for this issue.
551 5.7.1 The message was rejected due to classification as Virus, Spam or high bulk ratio.
This is a bounce-back message that you receive when an email is classified as spam while sending out. If you feel that a genuine email is rejected as spam, you need to send the same email with the full headers and the content to our support team. That email in question will be reviewed manually.
552 5.3.4 Message size exceeds fixed limit
A 552 email error is typically encountered when there is a problem related to an attachment in your email. Either it has exceeded the size limits of the remote server, or the file-type isn’t allowed by the remote server.
1. For file extensions not allowed on our servers, please do refer to the following link: http://support.mailhostbox.com/file-extensions-that-are-not-allowed-as-attachments/
2. For mail (including attachment) sent across from our servers, we allow clients to send up to 30 MB of data.
Solution: Examine the size of the message including attachments. Try zipping the file content.
553 5.7.1 Sender address rejected: not owned by user [email protected]
This is the error message that is received when you are trying to send an email as a different user. This error message is seen by the users who are using Exchange servers with our system.
You need to add an identity for the same in the webmail. For example,
Log into the webmail of [email protected]
Add the identity from the settings tab for [email protected] (If the from address is [email protected]). For more information, please refer: http://support.mailhostbox.com/email-users-guide/sender-identities
Once the identity is added and confirmed, you should be able to send the emails.
554 5.7.1 Service unavailable; Client host X.X.X.X blocked using zen.spamhaus.org;
This is the error message that is received of the IP address of the sender is listed at zen.spamhaus.org
For further details, please check http://www.spamhaus.org/zen
OR check http://www.spamhaus.org/query/bl?ip=<your_ipaddress> and contact zen.spamhaus.org to get the IP De-listed.
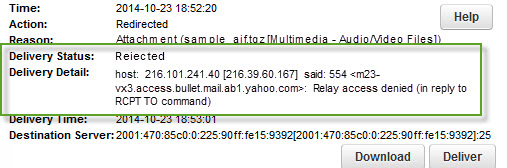
554 5.7.1: Relay access denied;
There are couple of reasons for this error while sending an email
If the domain is in the status “Pending Verification” in the control panel.
If the user has not checked the option “Our server requires authentication” option while setting up the account. For more information on setting up the email account, please refer: http://support.mailhostbox.com/email-users-guide/configure-your-desktop-…
554 5.7.1: Recipient address rejected: USER IS SUSPENDED
This error comes if a user is suspended in Control Panel.
554 5.7.1: Sender address rejected: Access denied.
This error comes when the sender address is blocked on our server. Generally, this is done if spam has originated from this user.
554-mx1.mailhostbox.com ESMTP not accepting connections OR 554-us2.mx1.mailhostbox.com ESMTP not accepting connections OR 554-in.mx1.mailhostbox.com ESMTP not accepting connections
When sending an email to a recipient within our mail hosting servers, sender may receive a bounce back stating ESMTP not accepting connections. The error indicates senders IP address is suspected of sending spam and is blacklisted.
Example Error:
Delivery has failed to these recipients or groups:
[email protected]
A problem has occurred during the delivery of this message to this e-mail address.Try sending this message again. If the problem continues, please contact your helpdesk.
Diagnostic information for administrators:
Generating server: mx1.mailhostbox.com
[email protected]
554-mx1.mailhostbox.com ESMTP not accepting connections
To resolve this issue, please perform the steps below:
1. Check sender’s IP address, if it is blacklisted in any RBL (Realtime Black List): http://mxtoolbox.com/blacklists.aspx. Ask sender to submit an IP removal request to RBLs.
2. Check IP reputation on mail filters by contacting CSI and get the IP delisted by visiting the following URL: https://csi.cloudmark.com/en/reset/ by providing the sender’s IP address.
200 Codes
- 211 – System status/system help reply
- 214 – Help message
- 220 – Domain service ready
- 221 – Domain service closing transmission channel
- 250 – Requested mail action completed and OK
- 251 – Not Local User, forward email to forward path
- 252 – Cannot Verify user, will attempt delivery later
- 253 – Pending messages for node started
300 Codes
- 354 – Start mail input; end with.
- 355 – Octet-offset is the transaction offset
400 Codes
- 421 – Domain service not available, closing transmission channel
- 432 – Domain service not available, closing transmission channel
- 450 – Requested mail action not taken: mailbox unavailable. request refused
- 451 – Requested action aborted: local error in processing Request is unable to be processed, try again
- 452 – Requested action not taken: insufficient system storage
- 453 – No mail
- 454 – TLS not available due to temporary reason. Encryption required for requested authentication mechanism
- 458 – Unable to queue messages for node
- 459 – Node not allowed: reason
500 Codes
- 500 – Syntax error, command unrecognized
- 501 – Syntax error in parameters or arguments
- 502 – Command not implemented
- 503 – Bad sequence of commands
- 504 – Command parameter not implemented
- 510 – Check the recipient address
- 512 – Domain can not be found. Unknown host.
- 515 – Destination mailbox address invalid
- 517 – Problem with senders mail attribute, check properties
- 521 – Domain does not accept mail
- 522 – Recipient has exceeded mailbox limit
- 523 – Server limit exceeded. Message too large
- 530 – Access Denied. Authentication required
- 531 – Mail system Full
- 533 – Remote server has insufficient disk space to hold email
- 534 – Authentication mechanism is too weak. Message too big
- 535 – Multiple servers using same IP. Required Authentication
- 538 – Encryption required for requested authentication mechanism
- 540 – Email address has no DNS Server
- 541 – No response from host
- 542 – Bad Connection
- 543 – Routing server failure. No available route
- 546 – Email looping
- 547 – Delivery time-out
- 550 – Requested action not taken: mailbox unavailable
- 551 – User not local; please try forward path
- 552 – Requested mail action aborted: exceeded storage allocation
- 553 – Requested action not taken: mailbox name not allowed
- 554 – Transaction failed
Extended SMTP (ESMTP) standards
The Extended SMTP error codes work in 3 digit combinations. For example, 5.2.1 is a Permanent Error where the receiving email is not accepting messages. The first number is the email message status. The second 2 numbers pinpoint the exact information about the error.
- 2 Successfully sent the email;
- 4 Temporary problem when sending the email. The email server typically will try to send it again till it reaches retry timeout.
- 5 Permanent or Fatal error. This can be caused by a nonexistent email address, DNS problem, or your email was blocked by the receiving server.
Below is a list of the Extended SMTP error codes.
Reference by mailboxhostbox