MazarBOT: New Android Malware Steals SMSs and Wipes Phones
A new Android malware, known as MazarBOT, has been discovered in-the-wild and this dangerous sample has the capability to hijack an unsuspecting user’s smartphone. The malware gets into a victim’s phone with an SMS as follows:
You have received a multimedia message from +[xx] [xxxxxxxxxx]. Follow the link hxxp://www.mmsforyou[.]Net/mms.apk to view the message.
When we tried to access this embedded link at our Quick Heal Threat Research Labs, an APK was downloaded into the vulnerable phone. When analyzed, the APK was found to be an interesting malware strain with extremely dangerous capabilities.
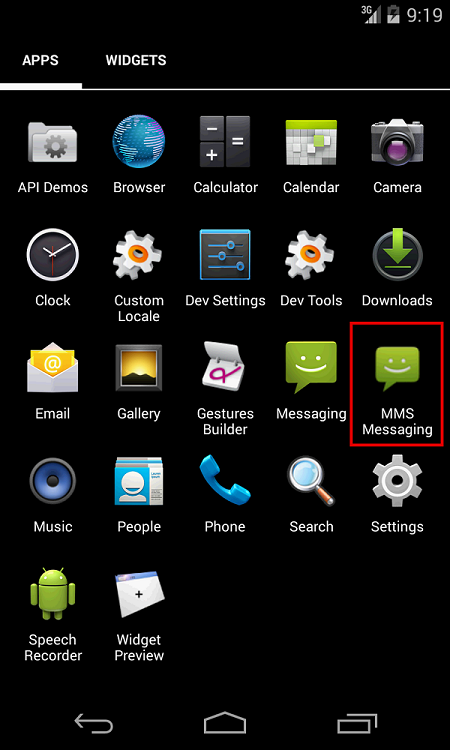
The wordings of the SMS are such that the user will be naturally inclined to click on the link that is included. Once the link is clicked, the APK starts downloading automatically and when this APK is then installed, the user can see the name “MMS Messaging” with an icon that is similar to the in-built Android SMS app.
After launching “MMS Messaging” a system prompt is shown as seen in Figure 2 below. This prompt allows the malware to get the privilege of a Device Admin. This privilege is the access right that is given by the Android OS to the malware in order to perform a factory reset of the device. To make the user believe that his permission is required to view the MMS, the malware shows the caption “Get video codec access”. Interestingly, once this page has been opened the user cannot back out or close the prompt. Even if the ‘Cancel’ button or the ‘Home’ button or the ‘Back’ button is pressed, the same window will open immediately until the user clicks on ‘Activate’.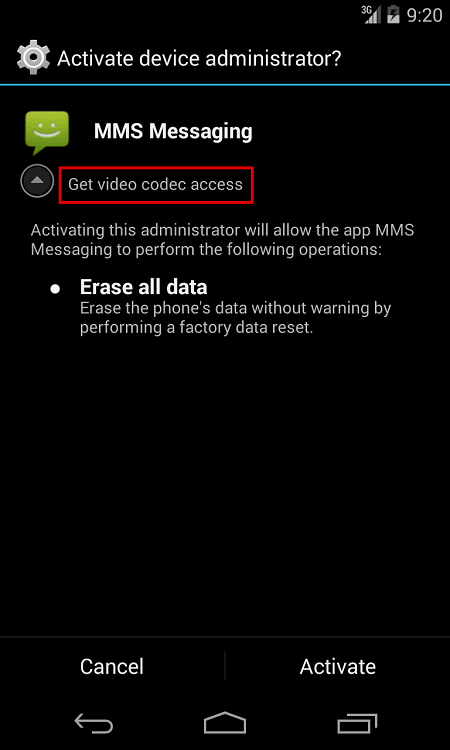
After clicking on ‘Activate’ the app icon gets hidden and the malware starts operating in the background. If the user now feels that something is wrong and tries to uninstall the malware, the process is complicated because the malware has Device Admin privilege. So to do so the user has to first deactivate that privilege. Unfortunately, the malware also has a way to prevent users from deactivating the Device Admin privilege.
Capabilities of MazarBOT to hide network traffic
Another integral feature of MazarBOT is that it makes use of TOR and Polipo Proxy libraries to hide its network traffic from monitoring tools that are used by security researchers. Its Command & Control server is located at hxxp://pc35hiptpcwqezgs[.]
Actions performed by MazarBOT in the background
- All incoming SMSs are forwarded to the C&C server. We sent an SMS to our test device and this SMS was intercepted by the malware and forwarded to the C&C server. That SMS was not visible on the device.

- MazarBOT can wipe all device data when it receives the “hard reset” command from the C&C server.
- It can send an SMS to any premium-rate number and this causes the user to get very high mobile usage bills.
- The malware can monitor which app is currently being used. If the app is of interest to the malware, it will show an HTML page that is similar to the app. This technique of “Fake Overlay Pages” can be used to steal user credentials of Gmail, Facebook or any mobile banking apps.
- The malware can inject itself into Google Chrome and can modify HTML content on open webpages.
- The malware can make calls to any number, reject incoming calls or enable call forwarding to numbers of its choice.
- It can lock the phone when it receives a ‘lock’ command. The phone will then remain locked until it receives an ‘unlock’ command.
List of C&C commands to MazarBOT
- Intercept Start
- Intercept Stop
- Stop Numbers
- Unstop Numbers
- Unstop All Numbers
- Lock
- Unlock
- Send
- Forward Calls
- Stop Forward Calls
- Update HTML
- Hard Reset
- Call
- Sleep
- Wakeup
How to remove MazarBOT
This malware cannot be easily removed in the traditional way because of its ability to get Device Admin privileges. Moreover, it does not allow users to easily deactivate that privilege. In order to get rid of the malware, the user will need to reboot the device in Safe Mode and then deactivate the Device Admin privilege. Only once this has been done can the user uninstall this malware from the device.
Quick Heal detects this malware on Android smartphones as Android.Mazarbot.A.
Courtesy: Quick Heal