77 Windows 7 Tips
77 Windows 7 Tips
Edited by Keith Ward
At a Glance:
- Make Windows 7 faster
- Get more done with Windows 7
- The best Windows 7 shortcuts
- Securing Windows 7
Contents
Windows 7 may be Microsoft’s most anticipated product ever. It builds on Windows Vista’s positives, and eliminates many of that OS’s negatives. It adds new functionality, too—all in a package that is less resource-hungry than its predecessor.
And whether or not you’re upgrading from Vista or skipping it altogether and moving up from Windows XP, you’ll need to know how to make the most of it in your environment. Here are 77 tips and tricks to get you there.
1. Pick Your Edition. Most business users do not need the more expensive Ultimate Edition; stick with Professional unless you specifically need BitLocker.
2. Upgrading? Go 64-bit. As the second major Windows release to fully support 64-bit, the x64 architecture has definitely arrived on the desktop. Don’t buy new 32-bit hardware unless it’s a netbook.
3. Use Windows XP Mode. Yes, it’s only an embedded Virtual PC with a full copy of WinXP—but it’s an embedded Virtual PC with a full copy of Windows XP! This is the first profoundly intelligent use of desktop virtualization we’ve seen—and a great way to move to Windows 7 without giving up full Windows XP compatibility.
4. Use Windows PowerShell v2. More than just a shell, this is the administration tool you’ve always wanted: Parallel, distributed processing for administrative tasks! Manage 100 machines literally as easily as you manage one with the new Remoting feature. Windows PowerShell v2 ships for the first time in Windows 7, and within six months will be available for older versions of Windows.
5. Use AppLocker. We’ve been fans of Software Restriction Policies since Windows XP, and AppLocker finally makes application whitelisting possible. Use it to enhance or even replace your anti-virus software, ensuring that only the software you want to run will run.
6. Shift to and from Explorer and CommandPrompt. The classic Windows power toy Open Command Prompt Here is now an integral part of Windows 7 Explorer. Hold down the shift key then right-click a folder to add this option to the property menu. While you’re in a command prompt, if you want to open an Explorer window with the focus of the window on the current directory, enter start.
7. Record Problems. The Problem Steps Recorder (PSR) is a great new feature that helps in troubleshooting a system (see Figure 1). At times, Remote Assistance may not be possible. However, if a person types psr in their Instant Search, it will launch the recorder. Now they can perform the actions needed to recreate the problem and each click will record the screen and the step. They can even add comments. Once complete, the PSR compiles the whole thing into an MHTML file and zips it up so that it can be e-mailed for analysis to the network admin (or family problem solver, depending on how it’s being used).
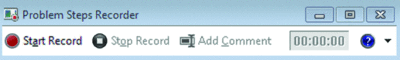
Figure 1 The Problem Steps Recorder dramatically speeds up troubleshooting. (Click the image for a larger view)
8. Make Training Videos. Use a tool like Camtasia to record short, two to three minute video tutorials to help your users find relocated features, operate the new Taskbar and so forth. Get them excited about Windows 7—and prepared for it.
9. Start Thinking About Windows Server 2008 R2. Some of Windows 7’s more compelling features, like BranchCache, work in conjunction with the new server OS. The R2 upgrade path is pretty straightforward, so there’s little reason not to take advantage of the synergies if you can afford upgrade licenses.
10. Prepare Those XP Machines. There’s no in-place upgrade from Windows XP to Windows 7, so start planning to migrate user data now, in advance of a Windows 7 upgrade deployment.
11. Consider Clean Installs. Even when upgrading Windows Vista machines, consider a clean install rather than an in-place upgrade. Yes, it’s more hassle, but it’ll produce a more trouble-free computer in the long run.
12. Consider Upgrade Assurance. Even if you’ve never bought it before, consider it for your new Windows 7 licenses. Access to the Microsoft Desktop Optimization Pack (MDOP), which includes App-V, MED-V and other cool technologies, is worth the premium.
13. Find New Tools. Within Control Panel is a single Troubleshooting link that leads you to all of your diagnostic tools on the system. There are additional tools, however, not installed by default. Selecting the “View all” link in the top left-hand corner will help you to see which troubleshooting packs are local and which ones are online. If you find a tool that you don’t have, you can grab it from here.
14. Understand Virtual Desktop Infrastructure (VDI). Windows 7 plays an important role in Microsoft’s VDI strategy, where virtualized Windows 7 machines are hosted on a central virtualization server using a special blanket “Enterprise Centralized Desktop” license. Read up and figure out if you can take advantage of this new strategy.
15. Prepare for DirectAccess. DirectAccess makes it easier for users to remotely access their office-based resources, without a VPN. DirectAccess also opens up remote computers more fully to Group Policy—but it requires Windows 7 and Windows 2008 R2.
16. Employ Deployment Image Servicing and Management (DISM). If you quickly want to list or manage Windows packages, features or drivers, use the command-line utility DISM. The “image” in the name may fool you into thinking that this is solely a deployment tool. An online command-line switch lets you manage the features in the currently loaded OS. To get a list of the loaded Windows features, enter dism /online /get-features /format:table. To enable a feature, enter dism /online /enable-feature /featurename:<name>.
17. Embrace Troubleshooting Packs. Designed to help users troubleshoot and solve problems on their own, you need to update your support procedures to acknowledge these Packs. For example, don’t force users to repeat steps the Pack already walked them through, and consider developing your own Packs (in Windows PowerShell) to support in-house systems.
18. Check Reliability. The Reliability Monitor was introduced in Windows Vista as ‘The Reliability and Performance Monitor.” In Windows 7 it has been separated from Performance Monitor and moved to a new location under the Action Center. You open the Action Center in Control Panel and then look under the Maintenance options for the “View reliability history” link. You can also just type in Reliability Monitor from the Instant Search (see Figure 2).
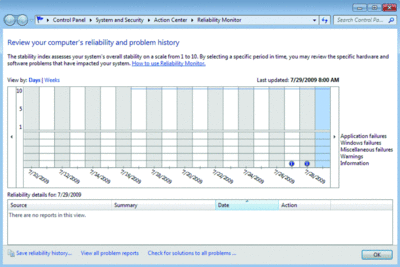
Figure 2 The Reliability Monitor has been broken out separately from Performance Monitor. (Click the image for a larger view)
19. Accept Diversity. Not every organization will be ready to move entirely to Windows 7 right away. That’s fine—but that shouldn’t mean the entire organization stays on Windows XP, either. The myths of the cost savings of having only one OS have been largely disproven or downplayed, so use Windows 7 where it makes sense to do so.
20. Get Snippy. The snipping tool has also been around in various incarnations but it’s even easier to use in Windows 7. Launch the tool, then drag and drop any part of your screen. The tool will snip the selection. You can save it as a graphic file or annotate with basic drawing tools. Teach your end users how to use this tool so they can grab the snapshots of their problems and send them to the help desk. Or create your own library of visual notes.
21. Presentation Nirvana. Press Windows+P to access the new Presentation mode, and easily turn on your projector and laptop screen at the same time. No more messing with vendor-specific utilities and arcane keystrokes. (Windows+X accesses the Mobility Center, with additional presentation options.)
22. Cut the Clutter. Press Windows+Home to minimize all but the current window, removing background clutter and letting you focus on that report your boss has been bugging you about.
23. Be a Mouse-Click Administrator. Windows 7 makes it easy to gain admin rights with a keyboard shortcut. Click on Ctrl+Shift on a taskbar-locked icon, and voila! You’ve launched it with appropriate admin rights.
24. Faster Installations. If your computer is capable of booting from USB, try this: XCopy the Windows 7 installation DVD to a sufficiently large USB drive, boot from that drive, and install Windows from there. It’s faster than a spinning platter.
25. Burn Discs with a Click. Or two; double-click an ISO file to burn it to your CD or DVD writer.
26. Restore Point Previews Many of us used to shut off System Restore because we were terrified to actually use it; under Windows 7, we can be much calmer. After selecting a Restore Point, Windows will now offer to show you which files and folders will be affected by restoring to that point.
27. Sync Time Zones. If you work with offices in different time zones and frequently find yourself missing meeting times because you are not in sync with their time zone, try the “Additional Clocks” feature that was first introduced in Vista. Within your Date and Time settings is a tab called Additional Clocks, where you can add two or more clocks to your taskbar time, and set them to provide different time zones from your current time zone.
28. Configure User Account Control (UAC). Even if you’re a UAC hater, give it another try. Go to the Control Panel to configure its behavior to something slightly less obnoxious than what Windows Vista had, and see if you can’t live with the extra protection it offers (see Figure 3).
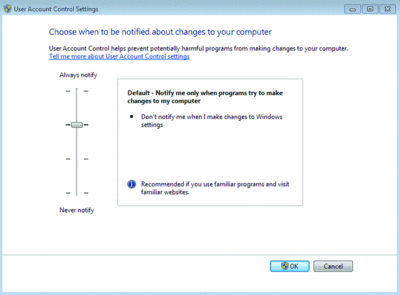
Figure 3 User Account Control, the bane of administrators, has been revamped and improved. (Click the image for a larger view)
29. RoboCopyCopyCopy. The always-useful Robocopy.exe can now run multi-threaded; run Robocopy /? to review its new parameters (like /MT for multithreading) and make your copies go faster.
30. Remote Desktop Console. Windows 7 Remote Server Administration Tools (RSAT) does not include a console-based remote desktop utility. And even if it did, the standard remote desktop console has some nagging limitations: It can’t move connections around in the list; it can’t sort by folders and so forth. If you manage lots of servers from your Windows 7 workstation, try downloading a copy of mRemote from mremote.org. This donation-requested utility allows you to mix together a variety of remote control applications, including Citrix Independent Computing Architecture (ICA), Microsoft Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), Secure Shell (SSH) and rlogin. All host names are displayed in a standard tree control that can be divided into folders, sorted alphabetically, and allow you to assign different logon accounts and secure passwords to each connection.
31. Multiple Monitors. Windows 7 makes working with multiple monitors intuitive and flexible. There are a variety of shortcuts and mouse motions that flick windows from monitor to monitor. To make the most of this, you need lots and lots of screen real estate. Try one of the new QWXGA monitors from Samsung (tinyurl.com/qwxgasamsung) or Dell (tinyurl.com/qwxgadell). These 23-inch monitors have a 2048×1152 resolution, making it possible to put two full-sized pages on the same monitor. Pair them together and you’ll get enough space to have all your admin tools open along with Office, Visio, your intranet sites and a little note to your mom in Live Mail. Move your taskbar to the left or right side of the window instead of along the bottom to free up even more real estate.
32. Windows PowerShell Scripting. If you want to make the most of Windows PowerShell on Windows 7, you’ll need a quick way to build and debug scripts. Windows 7 comes with an interactive editor that allows you to try out cmdlets and test functions on the fly.
33. Drag-and-Drop Notification Icons. The redesigned notification area displays only a minimum number of icons; all other notification icons are moved to a side window. Rather than using the Customize option to select icons for the main display, you can drag-and-drop icons from the side window to the notification area.
34. Add Unindexed Shared Folders to Library. You can add UNC paths such as \servernamesharename to a Library, but the server must index the folder. If you want to add a UNC path to an unindexed server, you can create a symbolic link to the UNC path, then add the link or links to the library. Use the mklink command. For example, mklink HomeFolder \ServerNameHomefolder.
35. Simplify Cloned Machine Setups. You can’t run Sysinternals’ newsid utility to change the identity of a cloned Windows 7 machine (either a virtual machine or imaged PC). Instead, create a template installation then run sysprep /oobe /generalize /reboot /shutdown /unattend:scriptfile. Clone or copy this virtual machine file. When it launches, it will get a new SID and you can fill in the name. The reference for building unattended script files is at tinyurl.com/winunattend.
36. Snap That Aero. The Windows key is great for all your shortcuts. Now you can use it to work with the new AeroSnap feature in Windows 7. Select a window, hit the Windows key and a left or right arrow to snap the window to that half of the screen, or use the up arrow to snap it to the top of the screen.
37. Shortcut the Taskbar. The Windows key is great for shortcuts. You can select the Windows key and a number to correspond to items on your taskbar. So, if IE (for example) is the third icon on your taskbar (not counting the Start button), you can hit the Windows key and the number three to launch or open IE.
38. Manage Passwords. Control Panel includes a new application called Credential Manager. This may appear to be a completely new tool that allows you to save your credentials (usernames and passwords) for Web sites you log into and other resources you connect to (such as other systems). Those credentials are saved in the Windows Vault, which can be backed up and restored. However, you might see this as similar to a tool we have in XP and Vista. From the Instant Search, type in control /userpasswords2 and you will be brought to the Advanced User Accounts Control Panel, where you can also manage passwords for your account (see Figure 4).
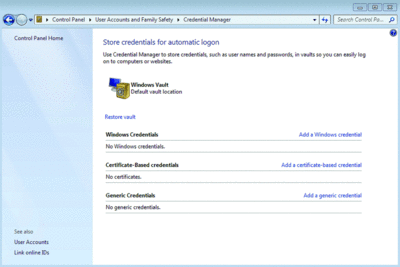
Figure 4 The Credential Manager provides a handy, secure place to store passwords. (Click the image for a larger view)
39. Trigger Actions. Event Viewer is closely tied into Task Scheduler. You have the ability to take an event (select it in Event Viewer) and then from the Actions pane, select the option “Attach a Task” to have that event, when it appears, trigger an action. That action can be: launch a program; send an e-mail; or display a message. This feature may be very helpful in troubleshooting a problem.
40. Browse InPrivate. A new feature in IE8 is the ability to open the browser in an InPrivate Browsing session that allows you to perform banking and so forth from a public location without fear of leaving behind any residue. IE will not retain anything you do in an InPrivate Browsing session. You can perform this action if you are already within IE by selecting the Safety button and then InPrivate Browsing. This will open another IE window altogether. However, you can save a few steps by using the shortcut. Right-click the desktop IE icon, click InPrivate and the windows will open in an InPrivate session already.
41. Go Live. Many applications installed on past versions of Windows have been removed. Starting with Windows 7, these applications (and a few others not typically installed with Windows) have been moved into the Live Essentials downloadable applications, at download.live.com. These applications include Messenger, Mail, Writer, Photo Gallery, Movie Maker, Family Safety and a few others.
42. Remove Apps. Although some applications have been moved off of Windows to become an optional download, other apps, such as IE8, Media Player, Media Center and DVD Maker are still included. In times past, especially when it came to IE, the applications were tied into the OS. However, in Windows 7 you can easily remove them if desired. Head to the Program and Features applet in Control Panel and select the “Turn Windows features on or off” link in the top left-hand corner. Then you can select the checkbox of the features you want to lose or add for your system (see Figure 5).

Figure 5 Windows 7 unbinds many applications from the OS, making it easy to add and remove them. (Click the image for a larger view)
43. Are You Windows 7 Experienced? System properties has a rating called the Windows Experience Index (WEI). This rating is a collection of five different ratings that are determined by the Windows System Assessment Tool (WinSAT). The highest rating score is 7.9 (compared to 5.9 in Vista), using the categories of Processor, RAM, Graphics, Gaming Graphics and Primary Hard Disk. The final rating is not an average of all the ratings, but the lowest of the subcomponent scores.
44. Analyze Processes. One of the coolest new features in the revamped Resource Monitor (resmon) is the ability to see the “wait chain traversal.” An unresponsive process will be shown in red in the Resource Monitor; right-click the process and choose Analyze Process. This will show the threads in the process and see who holds the resources that are holding up the process itself. You can then kill that part of the process if you like.
45. Create Virtual Worlds. Virtualization capability has been added to the Disk Management tools. If you open Computer Management, go to the Disk Manager tool and then click the Action button at top, you will see the options Create VHD and/or Attach VHD. This allows you to create and mount a virtual hard drive directly from within the GUI. Note: With Windows 7 you even have the ability to boot a Windows 7 VHD (see Figure 6).
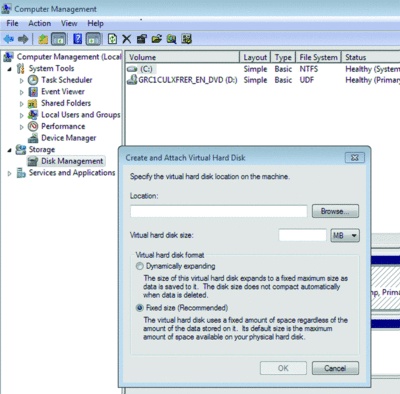
Figure 6 Windows 7 adds a great deal of virtualization support, including the ability to create and attach virtual hard drives from the GUI. (Click the image for a larger view)
46. Encrypt USB Sticks. Use BitLocker To Go. Maybe you’ve managed to never misplace or lose a USB key, but for the rest of us mere mortals, it’s a fact of life. Most of the time it’s no big deal, but what if it contains sensitive data? BitLocker To Go enables you to encrypt data on removable storage devices with a password or a digital certificate stored on a smart card.
The 14 Best Windows 7 Keyboard Shortcuts
The Windows key now performs a wide variety of functions. Here are a handful of the most useful ones:
64. Win+h – Move current window to full screen
65. Win+i – Restore current full screen window to normal size or minimize current window if not full screen
66. Win+Shift+arrow – Move current window to alternate screen
67. Win+D – Minimize all windows and show the desktop
68. Win+E – Launch Explorer with Computer as the focus
69. Win+F – Launch a search window
70. Win+G – Cycle through gadgets
71. Win+L – Lock the desktop
72. Win+M – Minimize the current window
73. Win+R – Open the Run window
74. Win+T – Cycle through task bar opening Aero Peek for each running item
75. Win+U – Open the Ease of Use center
76. Win+Space – Aero Peek the desktop
77. Ctrl+Win+Tab – Open persistent task selection window, roll mouse over each icon to preview item and minimize others
47. Lock with Group Policy. Take control through AppLocker application control. AppLocker intercepts kernel calls that try to create new processes or load libraries and ensures the code is allowed to execute. Practically, that means you can eliminate unknown and unwanted software by implementing AppLocker through Group Policy.
48. Be Our Guest. Guest mode proves a convenient method to give a guest or child access to your computer with limits on making system changes, installing software, or writing to the disk outside the user profile. After the user is done and logs off, data saved inside of the user profile is deleted. You cannot use Guest mode in an AD environment.
49. Restore from Backed up Restore Points. You can choose to include restore points in your backups and restore from them when using System Restore. This is convenient if you want to create a baseline of a working configuration and be able to restore to it in the future without overwriting other data on the hard disk.
50. Benefit from BranchCache. BranchCache helps you save on round trips for requested files in remote branch scenarios. If one person requests a file over the WAN, it’s cached locally and either distributed across computers at the remote branch or stored on a central server at the remote branch.
51. Disable Search Suggestion Popups. As you type in the Search Box, Windows 7 makes suggestions based on past queries by pulling past queries from the Registry. You can disable this in the Local Group Policy by enabling User Configuration | Administrative Templates | Windows Components | Windows Explorer | Turn Off Display Of Recent Search Entries In the Windows Explorer.
52. Pin Control Panel to Taskbar. If you use the Control Panel frequently, you may have noticed that you cannot simply right-click the Control Panel and select Pin to Taskbar. Instead, you must first Open Control Panel so its icon appears in the taskbar. From there, you can right-click the icon in the taskbar and select Pin this program to taskbar.
53. Leverage Search Connectors. You can now search the Web using the search functionality. Windows 7 includes Federated Search to increase the search scope beyond the local and network resources. Several search connectors are available, such as for YouTube and Twitter, or you can create custom ones to fit your needs.
54. Use Stickier Notes. Even though this feature has existed in previous versions of Windows in one form or another, it’s much easier to use in Windows 7. You can stick a note on your desktop for quick reminders. It’s a snap to change the font or note color. If you have a note selected, use Ctrl-N to create a new one.
55. Try out Improved WordPad. You probably haven’t given much thought to WordPad lately, but the version shipping with Windows 7 has undergone a major renovation. Think of it as a lite version of Microsoft Word. WordPad sports a spiffy ribbon interface, making it a snap to create well-formatted documents. Plus, you are no longer relegated to saving them as .RTF files. WordPad now supports the Office Open XML document (.DOCX) format. This makes it even easier to open .DOCX files created in Word in WordPad.
56. Calculate. Another basic utility that received a major overhaul is the venerable calculator. In addition to standard and scientific views, there are now programmer and statistic modes. You will also love the conversion and calculation features. Want to convert Celsius to Fahrenheit but can never remember the formula? Use the conversion panel. You’ll also enjoy the data calculation extension. Quickly find the difference between two dates or calculate a new date by adding or subtracting years, months or days.
57. Manage Services
from Task Manager. The Windows 7 Task Manager now includes a tab to manage services. You can quickly see at a glance the status of all services on your machine. Click a column heading to sort. You can even start and stop services with a simple right-click. If you need full-blown service management, use the Services button to launch the Services management console. You may often have the Task Manager running in the system tray; now, having service management access means one less window to have open.
58. Get Under the Hood. Windows 7 offers more ways to peek under the hood without adding third-party solutions. A terrific example is the Resource Monitor. The performance tab in Windows Task Manager is a good start, but sometimes you need more information. Click the Resource Monitor button to get more detailed information and performance graphs for key subsystems like CPU and Disk. You can also find the Resource Monitor under Accessories | System Tools.
59. Check Vital Signs. Another new system tool you’ll enjoy is the System Health report. In the Run dialog box, type perfmon /report, which generates a system health report. This report records details about your computer’s performance, resource usage and more. The report also includes diagnostic information about things that aren’t working as they should and suggested steps to resolve. The reports are saved and can be accessed with the Performance Monitor management console. You can also save as an HTML file or send via e-mail.
60. Get More Windows PowerShell. Windows PowerShell v2 promises to be a game-changer for many system administrators. Many will prefer to use the graphical Windows PowerShell console, also known as the Integrated Scripting Environment (ISE). You’ll find this in the Windows PowerShell folder under Accessories. Add a keyboard shortcut of Ctrl+Alt+I to quickly launch it. Run any Windows PowerShell command in the lower panel and see the results in the middle. Create or edit scripts in the top pane. Open multiple Windows PowerShell sessions connected to remote computers. The ISE makes Windows PowerShell v2 easy to use and fun (see Figure 7).
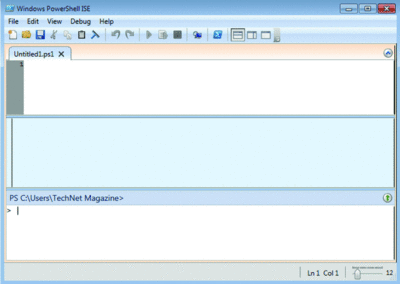
Figure 7 Windows PowerShell has been much more tightly integrated with Windows 7, and adds the Integrated Scripting Environment. (Click the image for a larger view)
61. Put It on Old Stuff. One perhaps-not-so-obvious Windows 7 tip is that you should attempt to install it everywhere. One user has a 6-year-old laptop that originally shipped with Windows XP. He could never get Windows Vista to install on it. But Windows 7 installed without complaint and runs extremely smooth. Granted, there are some Windows 7 features he can’t take advantage of because the processor lacks certain features, but these are minor issues considering the laptop now has life again.
62. Improve Security. In Vista it was difficult to manage system protection via restore points. The System Protection tab in Windows 7 is a vast improvement. In one spot you can configure how much space to devote to restore points, delete and create restore points or even turn off system protection altogether. This is very useful on older systems where disk space may be at a premium.
63. Actually Use Help and Support. Much of Vista’s clutter has been reduced in Windows 7. For instance, the Help and Support page has three links, a search window and a link back to Microsoft’s Windows site. It’s much less intimidating for end users, so make sure they know about it. Search is much improved as well, making for a better, faster experience.
A number of writers contributed to this article. They include:
Bill Boswell is a Senior Consultant in Microsoft Consulting Services, Desert Mountain region.
Pav Cherny is an IT expert and author specializing in Microsoft technologies for collaboration and unified communication. His publications include white papers, product manuals, and books with a focus on IT operations and system administration. Cherny is President of Biblioso Corp, a company that specializes in managed documentation and localization services.
Don Jones is a co-founder of ConcentratedTech.com, where he contributes daily technical education articles on Windows, Windows PowerShell, SQL Server, and other Microsoft and related technologies. You can reach him through the Web site.
J. Peter Bruzzese, Triple-MCSE, MCT, MCITP: Messaging, is the co-founder of ClipTraining, a provider of task-based screencast training with a proprietary corporate Learning Management Solution (LMS) CT LMS 5.0. He’s the author of “Microsoft Windows 7 Unveiled” (Que, 2009). He can be reached at [email protected]
Jeffery Hicks (MCSE,MCSA,MCT) is an independent author, trainer, consultant and a Microsoft MVP for Windows PowerShell. He is the co-author and author of several scripting-related books and perhaps best known for his Mr. Roboto and Prof. PowerShell columns. Follow Hicks at jdhitsolutions.com/blog and twitter.com/jeffhicks.
Courtesy :-
http://www.stumbleupon.com/su/1nALGl/technet.microsoft.com/en-us/magazine/2009.10.77windows.aspx
