Setting Up Your POP or IMAP Email Address in MS Outlook Express
To Set Up Your E-mail Account in Microsoft Outlook Express
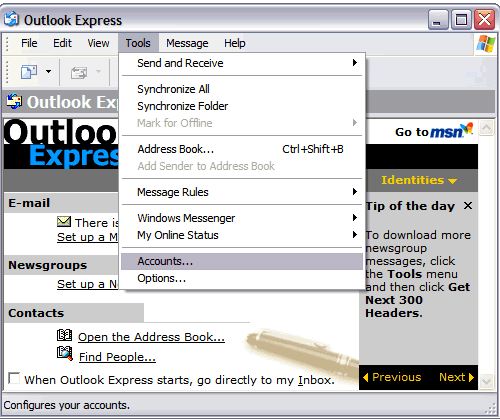
- In Microsoft Outlook Express, from the Tools menu, select Accounts
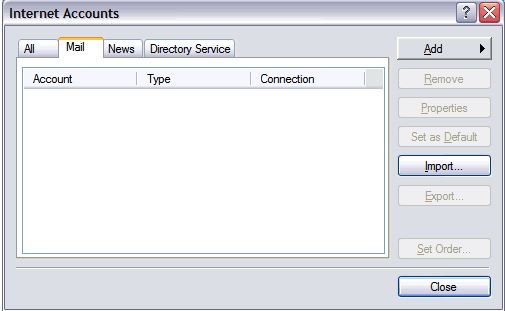
- Go to the Mail tab and from the Add menu, select Mail.
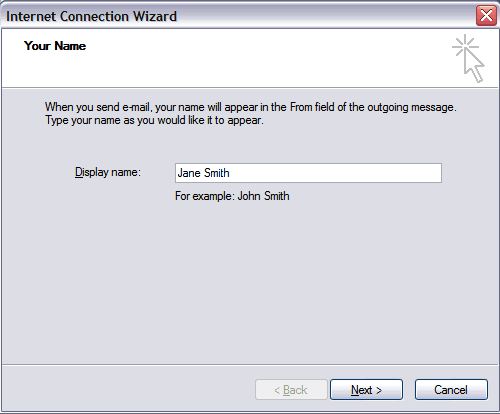
- In the Display Name field, enter you full name and click .
- In the E-mail address field, enter your email address and click Next.
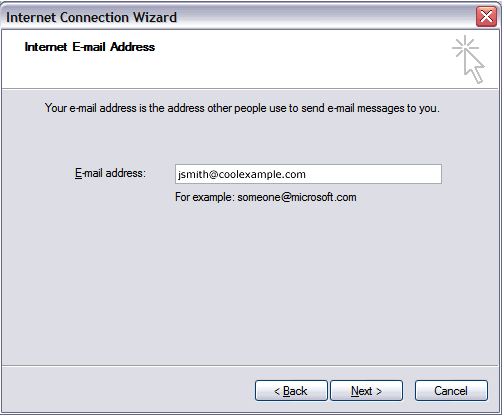
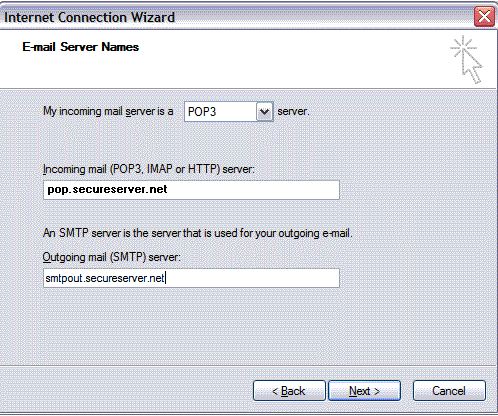
- On the E-mail Server Names page, complete your information as follows:
- My incoming mail server is a POP3 or IMAP.
- Incoming mail (POP3, IMAP or HTTP) server
- POP pop.secureserver.net. or IMAP imap.secureserver.net.
- Outgoing mail (SMTP) server
- smtpout.secureserver.net.
Click Next.
NOTE:“smtpout.secureserver.net” is an SMTP relay server. In order to use this server to send e-mails, you must first activate SMTP relay on your e-mail account. Log on to your Manage Email Accounts page to set up SMTP relay. If you do not have SMTP relay set up and your Internet Service Provider (ISP) allows it, you can use the outgoing mail server for your Internet Service Provider. Contact your Internet Service Provider to get this setting.
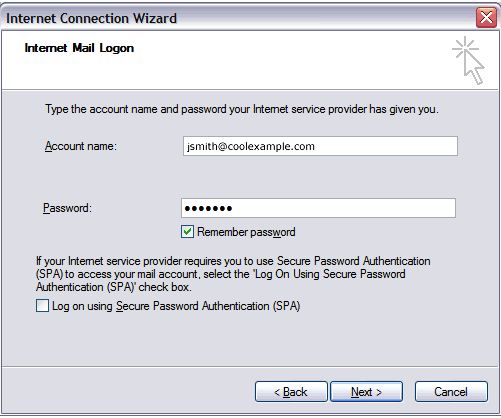
- In the Account Name and Password fields, enter your email address and password, and then click Next.
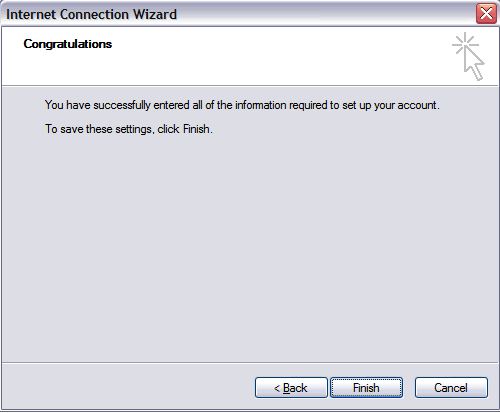
- On the setup confirmation page, click Finish.
- On the Mail tab, select the account you just created, and then click Properties.
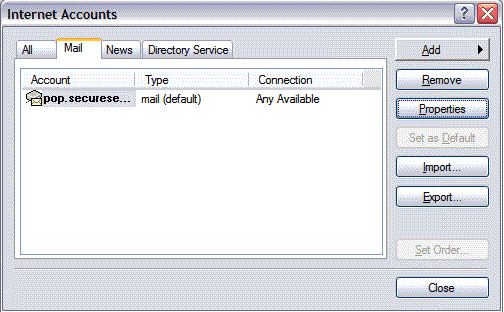
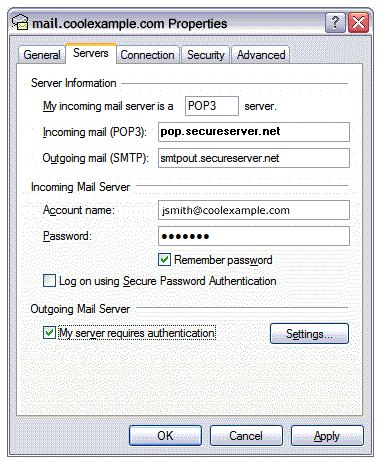
- Go to the Servers tab.
- Select My server requires authentication, and then click Apply.
- Go to the Advanced tab.
- In the Server Port Numbers section, change Outgoing mail (SMTP) to 80, and then click OK.
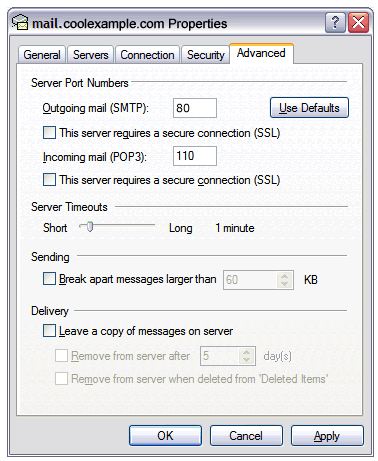
- (Optional) If you want to keep a copy of email messages stored on your email provider’s servers, in theDelivery section, select Leave a copy of messages on server.
Your Outlook Express account is now set up. Click Close to close the Internet Accounts window and return to your Outlook Express.
courtesy: secureserver.net
courtesy